What Is Mobile Threat Defence (MTD)?


Mobile threat defence is a set of actions and solutions aimed at protecting mobile devices, networks, and applications from cyber threats. And when a smartphone stores our entire lives — from entertainment to bank accounts — data protection is a hot topic of discussion. Companies are particularly attentive to this issue and try to ensure a universal and specialised approach to corporate network security.
Among the reasons for implementing MTD is the increase in fraudulent schemes, cyberattacks, and data theft. However, another reason is that company employees use personal mobile devices for work. And they also require security solutions similar to corporate ones.
Mobile threat protection is a whole algorithm of dependent actions that works in a state of constant analysis and search for suspicious activity. That is why its mechanisms are focused on three components: mobile devices, network, and applications.
MTD constantly scans devices and checks for discrepancies in OS versions, configurations, firmware, and system settings. The goal is to identify incorrect settings and potential vulnerabilities. Some companies that allow their employees to use personal mobile devices provide additional recommendations and requirements for device settings and use for work. Mobile device users are still the most vulnerable node in the system, so MTD solutions are designed to reduce the risk of cyberattacks.
Mobile threat detection activities on the network are aimed at detecting abnormal signs in traffic flows. Whether it is public Wi-Fi or an internal network, companies that work with sensitive data must ensure its security. The analysis mechanism is aimed at finding fake and invalid certificates and stopping attack attempts.
The MTD application protection suite is designed to analyse code and reverse engineer applications. The system can block an application if it detects suspicious factors or dangerous behaviour. Mobile threat defence solutions function as a unified system that covers all aspects of the mobile environment, from programme behaviour to network connections. Continuous updates based on threat feeds and analytics allow these solutions to adapt to new threats and stay one step ahead of attackers.
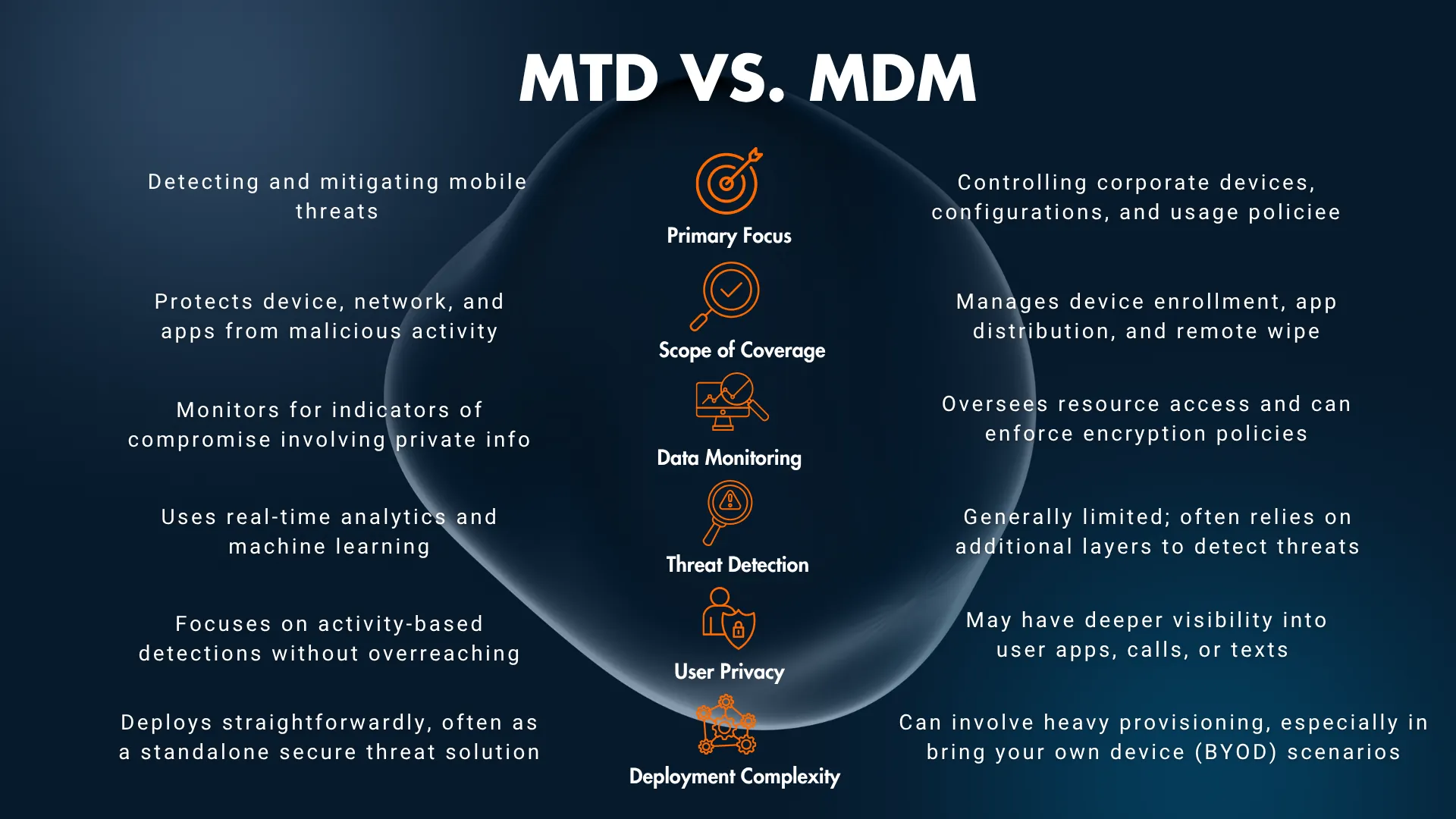
When it comes to MTD, MDM is often mentioned as another important component of digital security. MDM (Mobile Device Management) involves organising measures to manage devices and ensure security policies are followed. It covers organisational, advisory and direct rules for company employees regarding the use of devices, networks, and applications. MDM is not a tool for detecting and blocking threats (unlike MTD), but rather reduces vulnerability to them.
Digital security always requires a comprehensive approach involving technology, training, corporate culture, etc. Therefore, mobile threat detection will be highly effective under certain conditions.
Assessment of vulnerable areas and audit of current security tools. A set of actions aimed at finding weak areas in the company. Certain types of companies or large corporations may hire specialists who deliberately simulate cyberattacks of varying intensity and direction, specifically to identify vulnerable nodes. Such tests can last from a couple of weeks to months. Based on the results obtained, the company and technical specialists develop their own mobile threat protection strategy.
Implementation of Zero Trust in mobile device protection. The motto of this approach is: “trust nothing, verify everything.” This means that every device is considered potentially dangerous and is verified. Every request for access to corporate data or services requires authentication and authorisation, regardless of the device’s location. Access to resources is granted on the least privilege basis to minimise the risk of data leakage. An important component is network segmentation, which prevents the spread of threats.
Regular updates. This aspect applies to both the system and the rules. Regular review of current system solutions and technologies with their subsequent updates is the key to the success of a modern security system.
Seamless integration. The company must ensure the coordinated and unified operation of the local network and cloud environment, as well as integrate Zero Trust with MDM and EMM solutions.
Training of employees, familiarisation with information security rules. After implementing the changes, the company should conduct training to familiarise employees with the system’s features, security rules and conditions of use. Each new employee should also be familiarised with all aspects of the company’s cybersecurity.ії.
Cybersecurity would not have developed so rapidly if the specifics of cyberattacks and digital fraud had not evolved. These closely related areas modernise each other. Therefore, we propose to highlight common threats to corporate data.
Mobile threat detection actions help companies prevent, detect, and stop threats to digital data security and offer several benefits:
❖ Continuous analysis of the environment and its components
❖ Data protection
❖ Reducing the burden on IT
❖ System adaptability
❖ Anomaly detection
❖ Blocking potentially dangerous applications/links
There is no doubt that MTD has a future. The data security solution will only continue to evolve and modify. Companies are comprehensively integrating digital security strategies at various levels, and it’s only a matter of time before MTD is implemented. In the future, the speed of response to threats will increase, and the ability to automatically block malware and notify users of security anomalies will be automated. The MTD approach will likely increasingly involve AI and ML solutions to achieve high efficiency and automation.
One of the challenges of MTD is user privacy, and today, technicians and researchers are looking for solutions and privacy enhancements without losing the effectiveness of digital security solutions.
Implementing Mobile Threat Defense (MTD) in enterprises requires a comprehensive approach to ensure the security of mobile devices and corporate data. The first step is to integrate MTD with existing mobile device management (MDM) and SIEM systems for centralised control and threat monitoring. It is important to define clear policies for the use of both corporate and personal devices (BYOD), requiring the installation of MTD. Choose a solution that supports threat detection at the device, network, and application levels. It is equally significant to implement automatic response that blocks infected devices and notifies the IT department.
PNN Soft is an experienced company that offers modern strategies for protecting corporate data. We offer custom development from scratch and the implementation of additional solutions to existing systems. To enable us to assess and advise you on your request, please fill out the form below and our experts will contact you.