What is Zero Trust Security?


mes that are resistant to attacks, vulnerabilities and unauthorised access. It includes protecting code, data, runtime environments, and application interactions with other system components.. Security is important not only for corporate products and the protection of company data and employees. Individual users of commercial software are also increasingly concerned about security. There are some approaches to software security, with the choice depending on the solution type, project goals, and budget: Defence in Depth, Security by Design, PoLP, IDS/IPS, CSMA, etc. But we will focus on the question: “What does zero trust security mean?”
Zero Trust is a security framework based on the principle of creating a continuous check of all network entities, each device, user and application. “Zero Trust Network Access (ZTNA) limits access to specific applications or services based on successful authentication and contextual risk assessment. It isolates resources and ensures conditional, point-to-point access, making unauthorised actions significantly more difficult during a cyberattack. Hopefully, we have clarified what zero trust network access is, and now we can move on to the details of software protection.
Unlike traditional IT networks, Zero Trust operates consistently with hybrid and cloud environments. This approach also has higher requirements for policy controls and distrusts internal environment objects, thus securing each resource individually. The Zero Trust approach is used by government agencies, healthcare organisations, technology companies and financial institutions, which are the first adopters of this security concept.
Zero trust security solutions suggests that developers stick to established standardisation to ensure the reliability of the architecture.
There are certain principles that form the key elements of a zero trust architecture. These are constant verification, limiting the radius of influence from attacks, and automating the collection of environment context data. Let’s talk about each element separately.
1. Continuous verification. This principle is based on the main idea of Zero Trust: trust no one, check everything. This process is implemented through constant validation and monitoring. The system continuously assesses user behaviour and device compliance to ensure security. At first glance, this is a complex organisation of processes, but it is precisely this solution that helps to maintain flexibility and convenience.
2. Role-based access system. According to the principle of least privilege model, the user is granted minimal access, but sufficient to perform their tasks. This minimises surface attacks. Moreover, attribute-based access control doesn’t depend on VPNs, which is also the difference from the traditional approach which relies on the network location.
3. Zero trust framework uses micro-segmentation. ZTNA is based on the practice of dividing the system into small zones. There can be many elements in one network, but the user has access only to a certain part in his access zone. In addition, micro-segmentation increases the level of adaptability of the system to deployed policies. The principle of micro-segmentation is also an additional protection against lateral movement. Because Zero Trust access is partitioned and must be reestablished at intervals, an intruder cannot transverse to other micro-sectors within the system. When the presence of an intruder is identified, the affected device or user account can be isolated. Quarantine will deny further access.
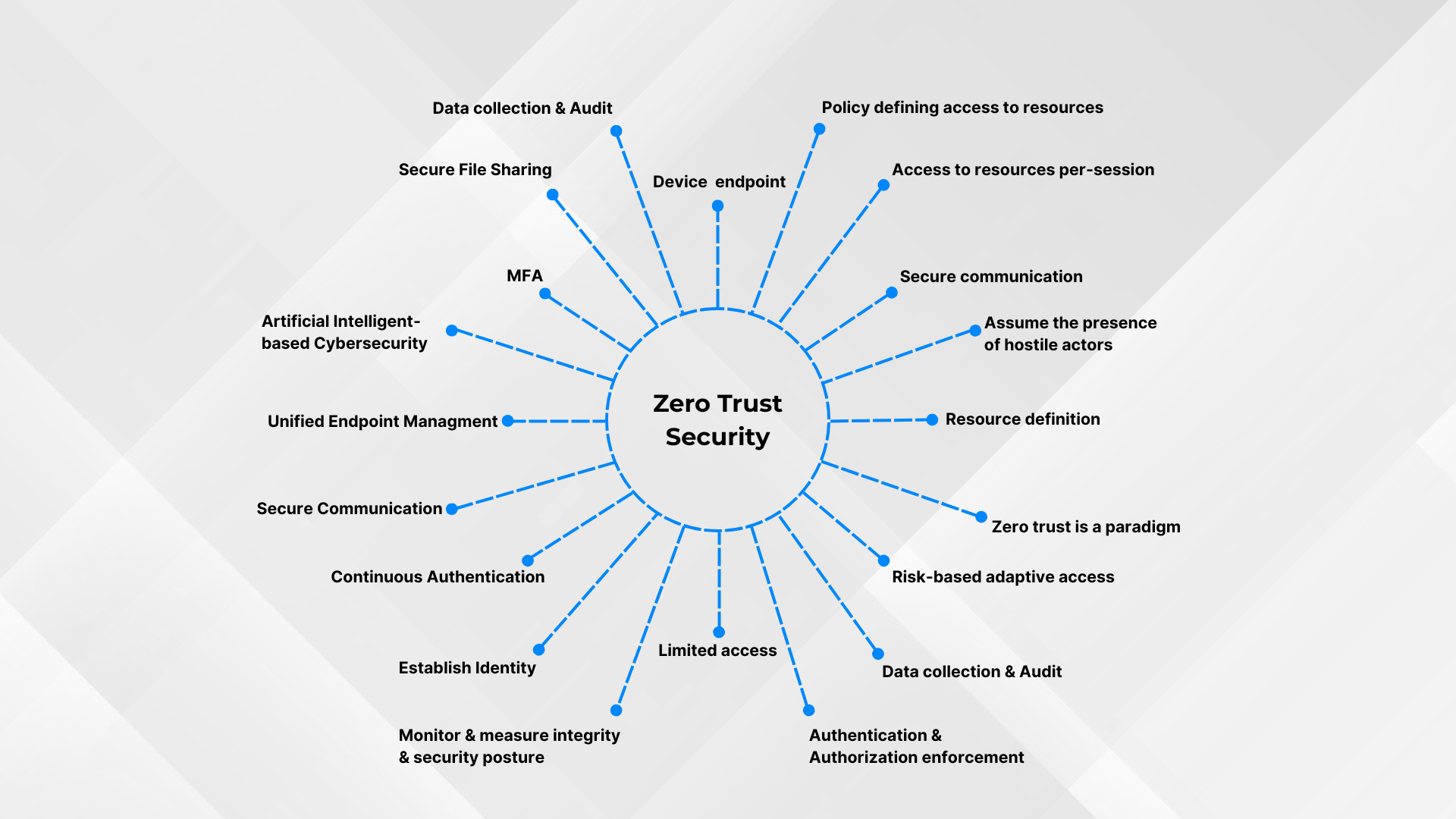
Zero Trust principles form the elements of the security architecture.
Identification and authentication
➤ MFA (multi-factor authentication), SSO, IAM systems. The software solution looks for more than two proofs of user identity.
Zero trust policy (Policy Engine)
➤ Access is granted only after verification of role, device status, and context.
Secure access to resources
VPN is replaced by ZTNA or SDP (Software Defined Perimeter).
Monitoring and analytics
➤ Continuous logging of actions, behavioural analytics, UEBA (User and Entity Behaviour Analytics).
Device status monitoring
➤ Check for updates, antivirus, encryption.
Microsegmentation
➤ Dividing the network into isolated zones with minimal access.
Zero Trust architecture is a security framework that requires all users, whether inside or outside the organization’s network, to be continuously authenticated, authorized, and validated for security configuration and posture before being granted or maintaining access to applications and data.
The Zero Trust architecture can be implemented through an enterprise infrastructure and a cloud platform. Implementation for corporate Zero Trust security software development is based on the following scheme:
[User] —→ [ZTNA Gateway] —→ [Policy Engine (IDP + Context)] —→ [SaaS/Internet/DB]
↓ ↑
[Monitoring the device status] ←— [SIEM/UEBA]
Implementation for cloude platform Zero Trust security software development is based on the following scheme:
[User] —→ [SSO + MFA] —→ [Policy Engine (IAM + Context)] —→ [Cloud (SaaS, API, DB)]
↓ ↑
[Monitoring the device status] ←— [SIEM / UEBA / SOAR]

Another factor in a good Zero Trust implementation is the task of automating context gathering. Zero Trust emphasises the automation of context collection and real-time response. Thus, the security system responds quickly and accurately to potential threats and collects the following data:
1. User credentials and user-related data.
2. Workloads.
3. All endpoint devices
4. Network traffic
5. Access to data
6. Integration with other security systems
Zero Trust cyber security provides maximum control, flexibility and security, especially in cloud and hybrid environments. Compared to the perimeter model, ZT radically reduces the risk of internal network compromise. Compared to Defence in Depth, ZT has a more adaptive and contextual access policy. Even compared to Cybersecurity Mesh Architecture, ZT is easier to implement at the resource access level.
| Type | Traditional perimeter security | Defense in Depth | CSMA | Zero Trust |
| Trust in the internal network | ✅ | Partially | ❌ | ❌ |
| Control at the user/request level | Low | Medium | High | High |
| Flexibility in cloud environments | Limited | Limited | High | High |
| Possibility of micro-segmentation | Absent or complex | Partially | High | High |
| The principle of minimum access (PoLP) | Optional | Partially | ✅ | ✅ |
| Resistance to lateral movement | Low | Medium | High | High |
| Identity orientation | ❌ | Partially | ✅ | ✅ |
| Security automation | Minimal | Partially | High | High (SOAR, UEBA) |
| Suitability for remote work | Low | Medium | High | High |
ZTNA
A mechanism that provides secure, controlled access to applications based on verified identity, device state, location, and other contextual factors. There is no direct connection between the device and the internal network. Authentication and authorisation takes place before each access.
JIT
Just-in-Time Access provide temporary access to resources only for the period when it is needed, with automatic revocation after the session. In this case, the admin gets access to the production server only for a certain period of time. The zero trust access significantly reduces the risk of account misuse or compromise.
SDP
Software Defined Perimeter is an approach that hides infrastructure from public view until the user is authenticated and authorized. It also reduces the attack surface because services are ‘invisible’ to attackers. And it is highly suitable for critical infrastructure, private APIs, etc.
DevSecOps
Integrating security principles into all stages of the software development lifecycle: from design to deployment. in this case, Zero Trust works not only at the access level, but also within the applications themselves. It also helps to identify and fix vulnerabilities even before production.
Zero Trust is critical because it addresses today’s cybersecurity challenges, where threats come not only from the outside but also from within the network. Compared to traditional approaches, this one offers granular control of zero-trust authentication based on user identity, context and behaviour rather than trust in network location. Implemented through tools such as ZTNA, SDP, JIT access, and DevSecOps, it significantly reduces the attack surface, minimises the risk of lateral movement of attackers, and provides flexible protection in cloud and hybrid environments. This makes Zero Trust not just a technical concept, but a strategic necessity for modern organisations.