How to enhance the security of cloud applications


It’s fair to say that video conferencing and remote work have accelerated a transition to cloud solutions as never before. Accessing updates, a flexible working process, scalability, and considerably low costs are far from a complete list of cloud benefits. Statistics claim that 40% of US and European business applications are placed in the cloud, and this number is expected to reach 70% in the next year.
A cloud service model has three main options: Software as a service (SaaS), Infrastructure as a service (IaaS), Platform as a service (PaaS). Unlike traditional IT, in these cases, applications and sensitive data flow through a third party. Each kind of solution has a different level of responsibility when it comes to providing data security. So before maintaining a security strategy, let’s dwell on it in more details:
And what about the responsibilities of providers? In a nutshell, they’re related to patching, the physical network, the storage, and the physical hosts’ configuration. Tracking potential threats and updating the infrastructure of your service helps public cloud providers accomplish their security goals. Clouds face the same hazards as standard data centers because they also run on software. Indeed, when you shift operations and assets to the cloud, your company loses some parts of visibility and control. Yet, several steps will allow you to manage business processes without being worried about essential information security. It’s time to dive into considering cloud-centric vulnerabilities and ways of reducing the risks.
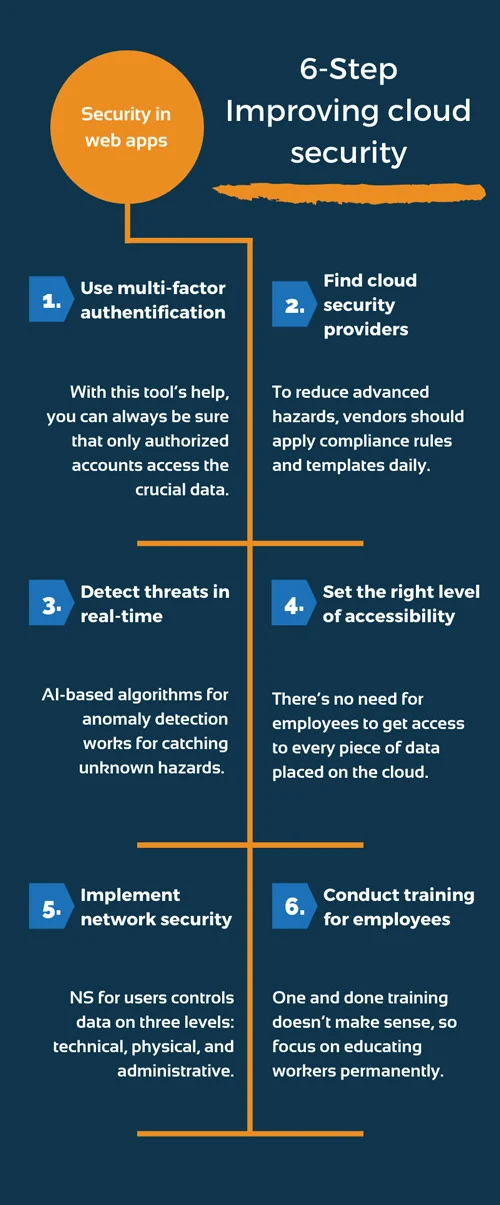
In the modern IT landscape, username and password are not enough for users’ account protection. If you want to prevent credential theft and provide security in web apps, multi-factor authentification is necessary. With this tool’s help, you can always be sure that only authorized accounts access the crucial data. MFA is one of the most affordable yet reliable techs nowadays. So why don’t you start with it?
It’s crucial to find reliable cloud security providers who always control configuration errors. When it’s possible, the system deals with the consequences automatically. But anyway, to reduce advanced hazards, vendors should apply compliance rules and templates daily.
AI-based algorithms for anomaly detection works for catching unknown hazards. Then it’s time to analyze all the threats and evaluate the risk. Needless to say, that rapid error detection plays a role. Therefore, maintaining data security in the cloud is hard to imagine without real-time alerts on safe police breaches. We also suggest you think over implementing advanced solutions, such as Vulnerability Scanning, Intrusion Detection and Response.
There’s no need for employees to get access to every piece of data placed on the cloud. First of all, setting an appropriate authorization level of authorization prevents workers from changing files they don’t need to edit. Plus, it guards your company against stealing employees’ credentials.
As a rule, this term includes virus and antivirus software, access control, application security, network-related security, VPN, and so on. Network security for users controls data on three levels: technical, physical, and administrative.
Hackers tend to resort to spoofing websites, phishing, and social media spying. The best solution for safeguarding staff members is to offer ongoing security sessions. But bear in mind that one and done training doesn’t make sense, so focus on educating workers permanently.
If you feel like using virtual private clouds appeals to your business more, test-drive AWS (Amazon Web Services). A cloud computing web-product helps companies meet primary compliance and safety requirements, namely protection, data locality, and confidentiality. By utilizing AWS, you can automate numerous manual security tasks and concentrate on achieving the business goals and scaling up your company. The multifunctionality of the platform is the result of the AWS infrastructure. It blends features of the platform as a service (PaaS), infrastructure as a service (IaaS), and packaged software as a service (SaaS).

There are several aspects to discuss with the vendors at the very beginning:
As soon as your cloud infrastructure is ready, you should schedule regular testing. The best way to execute testing is to cooperate with third parties agencies that conduct penetration tests. That step is critical for uncovering soft spots within the digital system.
Speaking about cloud computing key trends, we cannot mention a multi-cloud solution with public and private environments. In such a way, users can protect sensitive data on a private cloud while working with less-sensitive information in the public one. Artificial intelligence, IoT, cutting-edge serverless, and managed services also differentiate the top cloud vendors in 2020.

PNN Soft provides customers with the best software development outsourcing services. The company has 20 years’ experience in creating highly efficient solutions, but we are continually honing our skills to deliver advanced technologies. We have developed more than 1000 efficient and stable web-products for different industries, including mobile and desktop applications. Whatever option you select, the security of the solution is our primary concern.
We are determined to seek innovative solutions that meet individual companies’ needs. That is why we know which technologies spell success for your business.
PNN Soft takes full advantage of Scrum and Agile methodologies to ensure constant communication with customers and build a flexible manufacturing process. Our Agile-teams of professionals include software developers, testers, GUI designers, technical writers, and managers.
Check out the portfolio for a better understanding of the web-products we create. And if you want to implement a cloud solution, take the initial step by filling in the form below.