Achieving Security Compliance with DevOps and DevSecOps


This article will help you understand the difference between terms and their key features. It will be comprehensible for those who have previously encountered an order for the development of IT solutions and want to make their product more secure and who are faced with these definitions for the first time.
Millions of businesses use cloud platforms and Amazon Web Services, in particular, as it helps to achieve flexibility, lower costs, and give an innovative boost to your enterprise. In the cloud age, companies should diligently work on cybersecurity throughout the whole DevOps pipeline — that’s what AWS experts say. But what if you are eager to create a cloud platform that perfectly fits your company’s needs? Which approaches are indispensable for strengthening cybersecurity?
If you are planning to develop a custom cloud solution, think about implementing DevOps and DevSecOps methodologies. DevOps and DevSecOps allow all stakeholders to collaborate on every project stage. In such a way, developers, QA, and security teams join their efforts to evolve security systems promptly. Throughout the platform lifecycle, cybersecurity remains the primary focus of each expert. Both technologies allow clients to use automated policies, configuration management instruments, and fine-grained controls. The policy as code and infrastructure as code models are perfect for tracking compliance at scale.
Before focusing on the steps to get started DevSecOps, let’s clarify the difference between DevSecOps and DevOps.

Simply put, DevOps is about development+IT Operations+Application Delivery. DevSecOps implies Development+IT Operation+Security+Application Delivery.
Both of them encompass ideology, a system of practices and tools that enables companies to deliver solutions at high velocity. The traditional approach implies performing software development and deployment processes separately. By contrast, DevOps aims to eliminate the boundaries between these departments. As a result, the whole development process becomes more efficient: you optimize time, improve productivity and establish a constant collaboration flow.
DevOps philosophy contains three main approaches:
According to the DevSecOps philosophy, organizations should integrate security into every part of the DevOps lifecycle, from creating a layout to testing and supporting a released product. DevSecOps, as it were, is a part of DevOps, which has grown so much that it has become an independent ideology and a tool for integrating security into the development process. Engineers are responsible for the safe automation of all technical aspects of software product development( SDLC).

The transition to flexible cloud computing platforms shared data storage, and dynamic applications have unconditionally increased the production efficiency of processes in organizations from different fields of activity.
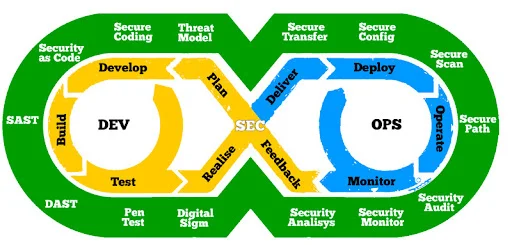
First of all, to create specific solutions for the cybersecurity of the product, it is necessary to simulate risks. Threat modelling is the root method of ensuring security. Understanding of potential threats will be reflected in the preparation of technical specifications, design, and testing. At the same time, this process is dynamic. The list of risks will increase, take on specific forms, and as a result, the team will be able to provide the highest quality tools for protecting the product.
A separate article can be devoted to the issue of security in the presented ideology. Each stage of SDLC has its own characteristics. However, we suggest that you familiarize yourself with the DevSecOps shared keys.

Planning of the project
Threat modelling, IDE security plugins, Pre-commit hooks, Secure coding standards, peer review.
Code’s commitment
Static app secure testing, security unit & functional testing, dependency management, and secure pipelines.
Build and Test
Dynamic app secure testing, Cloud configuration validation, Infrastructure scanning, and Secure acceptance testing.
Realize and Production
Secure Smoke Test, configuration test, and live site penetration testing.
Operate
Continuous monitoring, threat intelligence, IT penetration testing or pen test, review of the incident, and review of the team’s work on its resolution.
Integrating operations into your development process and vice versa isn’t enough for dealing with compliance issues. If your priority involves improving code quality and obtaining reliability assurance, start working with DevSecOps engineers from the very beginning. We’ve prepared a shortlist of practices that can hopefully be your starting point.
That’s why enterprise leaders have to cultivate security awareness. Put this issue on top of employees’ concerns — it will give you extra days to pause the deployment phase for penetration testing.
Ideally, DevSecOps engineers help other team members cover the basics of secure coding and explore more advanced security instruments. All employees should revisit training several times per year: the complexity of sessions grows respectively.
A WISP (written information security plan) and a DIRP (data incident response plan) will provide your colleagues with valuable insights if only they are clear and concise. Otherwise, they become an obstacle to understanding which encryption keys, cyphers, and passwords it’s better to use. After all, you want your team to become aware of essential security tools without being confused or distracted because of verbosity.
When a team has one solution per problem, it allows enterprises to save costs and enhance efficiency. Try to cooperate with IT experts skilled in custom development for particular industries — they have extensive experience in achieving compliance.
5. Penetration testing and code review comb every inch of your system.
You know nothing (or nearly nothing) about the system until you test it. It’s worth testing platforms during the deployment process, for sure. Yet, additionally, you may cooperate with separate departments to conduct penetration testing in a real-life environment.
PNN Soft has been delivering programming products for 20 years, and we hone our skills to provide our clients with reliable IT services. We implement management and security tools for compliance projects. Regardless of the industry segment, we aim to pay special attention to systems’ security.
We focus on achieving an in-depth understanding of an individual company’s goals, requirements, and suggestions. That is why our clients prefer long-term cooperation.
PNN Soft implements Agile, Scrum, and RAD methodologies to interact with clients effectively, meet customers’ expectations, and obtain more flexibility. Our teams of experts include software developers, DevOps and DevSecOps engineers, GUI designers, testers, technical writers, and managers.